
Security Advisory, July 29, 2025: Security Patches are now available
We recommend you upgrade to the latest patch

Who’s affected?
Versions affected:
-
Umbraco 13.0.0 - 13.9.2
-
Umbraco 15.0.0 - 15.4.3
-
Umbraco 16.0.0 - 16.1.0
Unsupported versions can be subject to the vulnerability, but will not receive a patch. We recommend upgrading to a supported major version.
As the vulnerability exists in the Content Delivery API, which was introduced in Umbraco 12, versions after this are affected.
How to fix the vulnerability
Patches are available for the latest minor versions of Umbraco 13, 15, and 16. As we are looking at a patch upgrade, and the fix is straightforward, we expect the update to only require minimal effort per project.
Instructions on patch availability and how to upgrade can be found in the release notes:
Automatic fix on Umbraco Cloud
All Umbraco Cloud sites running the latest minor version of a supported version are patched via the automated patch feature. The security patches will be rolled out to Umbraco Cloud today to ensure all sites have been fixed.
If a project is not running the latest minor version (13.9.x, 15.4.x, 16.1.x), the patch can be applied using the minor upgrade feature.
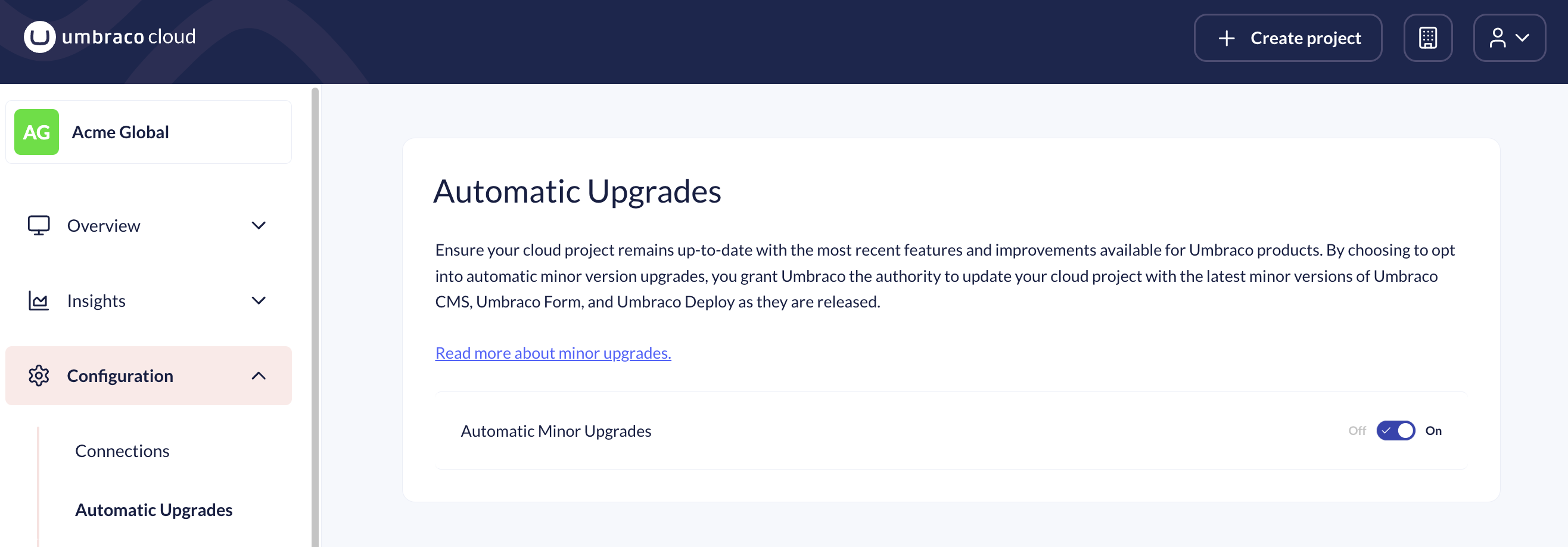
ℹ️ Note that Umbraco Cloud also supports automated minor upgrades. This can be enabled on a per-project level and ensures you're always ready to receive the latest patch.
What we know about the vulnerability
Umbraco's content delivery API can be restricted from public access such that an API key must be provided in a header to authorize the request.
It's also possible to configure output caching, such that the delivery API outputs will be cached for a period of time, improving performance.
There's an issue when these two things are used together in that the caching doesn't vary by the header that contains the API key. As such, it's possible for a user without a valid API key to retrieve a response for a given path and query if it has recently been requested and cached by request with a valid key.
For more details, please refer to the security advisory:
Impact
The vulnerability exists only for Umbraco installations configured to use the content delivery API with public access restricted and response caching enabled.
With that set up, it is possible to retrieve published and draft content that should be protected from public access, without a correct API key.
Credit
This vulnerability was discovered as part of internal testing.
Any questions?
If you have any questions or comments about this advisory, make sure to get in touch with us directly on the Security Advisories. Alternatively, you can reach out to the dedicated security email address listed at https://umbraco.com/security. Here you can also find information on how we handle security-related issues.
For direct communication related to security in Umbraco products, please sign up for the dedicated security mailing list.